How to protect your data and digital identity
In this webinar, our IT security champion Pavel Matějíček focused on several important topics in the field of cyber security. In the introduction, you can learn how to recognize phishing and avoid falling into the traps of modern cyber attacks not only via email. Next, the future without passwords was discussed – what alternatives await us and when will it come? Is it even possible? There was also talk about how to protect your online identity and what technology it is good to equip yourself with.
Webinar recording
How to spot phishing?
Recently, due to the increasing number of attacks, it has become more difficult to distinguish what type of fraud we are dealing with. So what exactly is phishing? It is one of the so-called social engineering methods that uses manipulation to get your login details or other important data. Those there are times when its recognition was easy. The attack was characterized by poor, broken, or machine-translated English, and this “improvement” is mainly due to the improvement of automatic translators.
The fraudulent email or message usually requires you to go to a fraudulent website where you log in, open a malicious attachment full of malware, etc. This either steals your login credentials or compromises the malware. The phishing will have served its purpose and you will have let yourself off the hook. These attacks are successful about 60% of the time.
Types of phishing
Familiar classics and current novelties
Here we have a classic that every user has seen at least once – an email arrives, written in such a way that everyone can find some part of it and is therefore easily believable. It still contains occasional grammatical errors, the click-through sometimes lacks an HTTPS certificate, and usually doesn’t target you personally. It can be an official email from an institution, a product offer, etc.
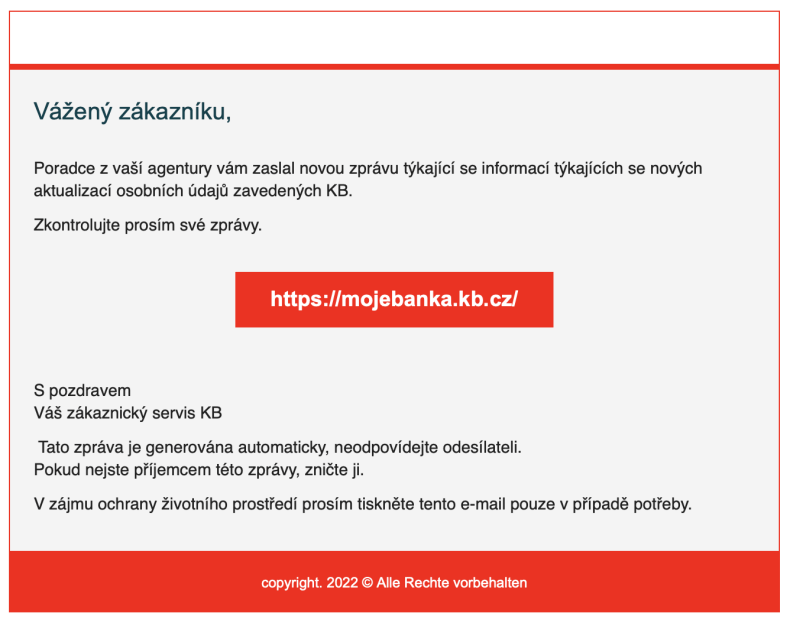
Then there is spear phishing, which is specific and targeted either at you or your organisation. So the attackers have already gone to some trouble to find out information about you and often impersonate someone you know. This type of phishing is professionally handled, the fraudulent sites have a valid certificate and are very difficult to distinguish from the genuine ones. The sender often uses so-called homoglyphs, i.e. characters that are very similar to each other so that you cannot tell them apart when you read them.
Phishing is no longer just emails
Before Christmas, we saw a mass load of smishing, i.e. phishing by SMS messages. With this type of attack, attackers try to bypass the anti-spam and anti-phishing tools that are on computers and rely on the fact that ordinary users do not have anything like this on their phones. Again, they use various tricks to get you to click through – copy this link into your browser, etc.

Vishing is not a scam message but a phone call designed to get as much information out of you as possible, which is then often used for the next attack. The other possibility is that the attacker is directly asking you to take an action – open an email, log in somewhere, download an app to your desktop…
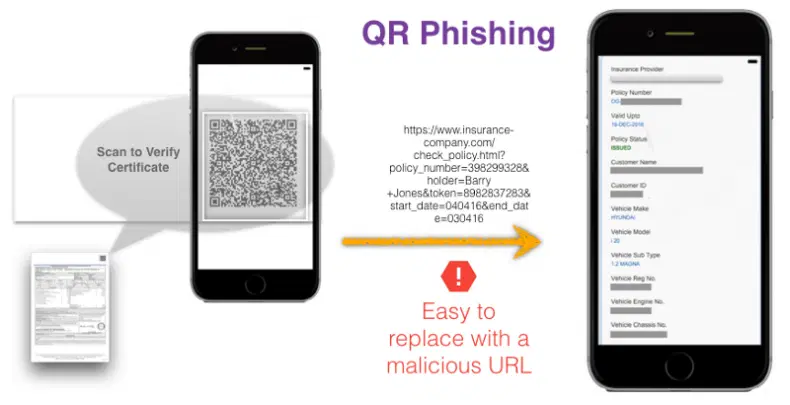
A hot new trend that is now enjoying unprecedented growth is quishing, a form of QR code fraud that takes you to a scammer’s site where you then lose your details.
Currently, we can also encounter many other models of social engineering that are no less insidious, such as the so-called OMG cable. This looks like a perfectly ordinary cable that you use to connect your phone to your computer, but the catch is that it can create a separate Wi-Fi hotspot that an attacker can connect to remotely and record everything you type, including passwords or other sensitive data.
Interested in more?
Phishing, quishing, SPAM and SCAM – what is what and how to know what it is
More about homoglyphs
Homoglyph Generator
URL Analyzer
Email Header Analyzer
VirusTotal
Is there a future without passwords?
The trouble with passwords is that they are needed in large numbers and are difficult to remember. A good secure password should be around 15 characters long, should be random and should contain a variety of characters. That’s why it is more than advisable to choose and use a password manager that will do the hard work for you, plus help you spot fraudulent sites. It is definitely not advisable to use the same passwords across all different user accounts!
How long will the passwords be with us?
But passwords will definitely be with us for a long time; many institutions and services still haven’t discovered two-factor authentication and still have passwords posted on monitors and the like. Some services are already approaching logging in with so-called “passkey.” A passkey is a digital record that securely links your information to a service using, for example, a fingerprint, facial scan, or other display lock to replace manual password entry. But then there are a number of services that don’t use this option and won’t for a long time.
Useful links
Password Manager – how to do it?
How secure is my password?
How long would it take to crack my password?
Sticky Password
Bitwarden
How to use bitwarden?
Passkey for iPhone
Passkey for Android
have i been pwned?
Why not use LastPass?
Digital legacy