Can your employees
Recognize targeted phishing? fraudulent calls? social engineering? a planted USB? fake invoices?
BOIT – IT Security and Protection
#doingbusinesssafer
Phishing has many faces. It’s not just about email.
Phishing is no longer just about fraudulent emails. Attackers today abuse a wide range of communication channels – from SMS and WhatsApp to Teams/Slack/Discord, social networks, QR codes or even fake calendar invitations. Advanced techniques such as deepfake voicemails or videos that mimic supervisors or colleagues are also becoming increasingly common, adding to the credibility of the attack.
The goal is always the same: to get the user to click, enter login credentials or execute malicious code. It is the variety of these channels that increases the risk of being caught out, even if someone has long been immune to classic email phishing.
Therefore, in our simulated attacks, we don’t just go after emails. We can simulate phishing via SMS, Teams messages, fake websites, QR codes on posters and deepfake scenarios. This allows employees to experience what phishing looks like in different forms and learn to spot it even where they wouldn’t expect it. The goal is not to catch, but to prepare – and the more realistic the scenarios, the better the prevention.
Our campaigns are professional. Take a look.
In our virtual mailbox you can test your observation. Start by clicking on your email.
We don’t use simulators –
we work as a real attacker
We will always customize the phishing scenario according to your needs and requirements.
You will not see any uneditable templates in English here.
How does the phishing test work?
You’ll be in touch with our phishing campaign experts throughout the testing period. From the initial consultation on the wording of the phishing message and the simulated target site (OWA, SharePoint, intranet, …) to the delivery of the final report and the domain used in the testing. After the launch of each campaign, you will receive interim results from us so that you have real numbers for management. We will also advise you on how to respond to questions and suspicions raised by users.
Scenario selection
For a successful attack, you need to choose the right scenario - that is, a story that motivates the employee to take the action the attackers want him to take.
Together, we select realistic scenarios and define the target groups to be targeted by the simulated attack.
We alwaystailor the scenarios to the customer or create a unique scenario for you in any language.
Setting exceptions
We can also do blacbox text, where we will monitor the response of your security systems, but it is better to set exceptions.
We are simulating the worst case scenario, when everything fails and phishers enter the company. We can then measure the success of campaigns without bias.
Set exceptionsStart of testing
We usually release the first phishing within three weeks of the request.
The average time to collect relevant results is one week. We keep you informed about how the campaign is going and whether everything is going according to plan.
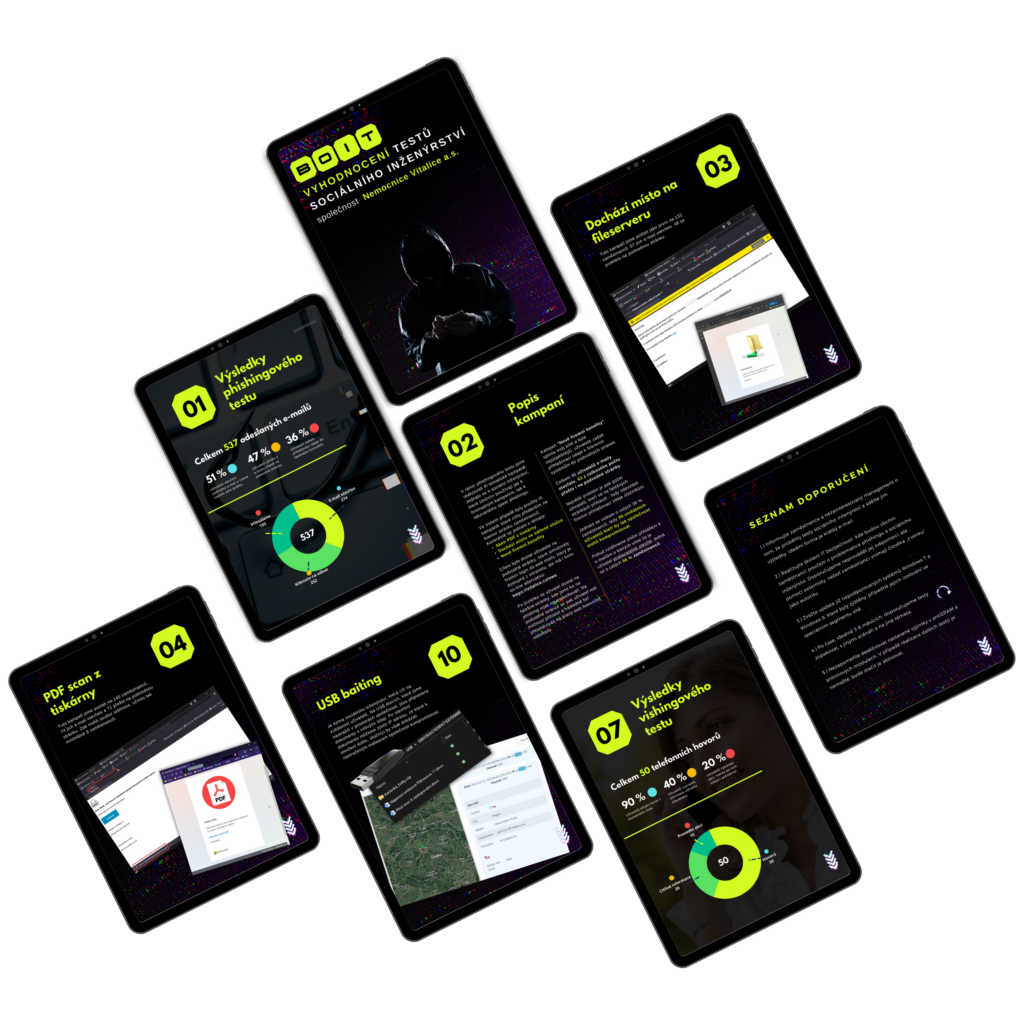
Clear evaluation
We measure how successful the campaign was - we find out how many users opened the message, how many clicked on the fraudulent link, at what time and on which device.
We'll also see how many employees have even logged into the fake portal.
The evaluation can be very detailed, where we can see which user, and at what position, entered what password into the compromised system, when and from where.
Sample of the final reportVerification of acquired knowledge
Repetition is the mother of wisdom, so it is not surprising that we recommend repeating the test after 3 to 6 months.
We have long-term contracts with several clients and test employees at random intervals throughout the year.
We can also send out an educational newsletter to employees after the campaign has been evaluated and follow up with education to raise security awareness.
InquireNIS2 is not a bogeyman. And the attackers aren’t waiting. Why should you?
The NIS2 directive is not about scaremongering, but an opportunity to increase business resilience. One of its pillars is working with the human factor – i.e. training and testing employees against threats like phishing. And simulated attacks are the most effective way to measure and mitigate these risks.
Deciding whether to test is no longer an option. Attackers don’t wait for legislation or budgets – they try it every day, through different channels and getting smarter. We can help you test your employees before an attacker does it for real.
Interested in more?
Pavel Matějíček talked about aspects of simulated phishing campaigns for O2 CyberNews magazine.
We test the security awareness of
employees comprehensively
We recommend supplementing the phishing test with the following social engineering techniques. This will give you a comprehensive view of employee behaviour, which will help you identify weaknesses in your cyber security.
Baiting
We will also check your employees for planted storage media in the company perimeter by baiting – planted USB drives in and around the workplace.
Vishing
Security mystery shopping. We’ll find out if your employees will trust us with internal information.
Quishing
QR codes can be misused by an attacker, for example on invoices. Test your accounting and processes.
Want to know more? Leave us a contact…
Interested in an employee phishing test?
Leave us your contact information. We will get back to you with a non-binding quotation.